Task 1 – What is the full path of the script used by Simon for AWS operations?
After unzipping the file and going through the folders there seemed to be four files in total:
- config.xml
- session.xml
- LootAndPurge.java@2023-07-24_145332
- YOU HAVE BEEN HACKED.txt@2023-07-24_150548
Using Notepad++ I was able to open all four files at once and easily navigate between them. After a little bit of analysis, I found that config.xml showed a history of which files were open. Within the history, we find the answer.
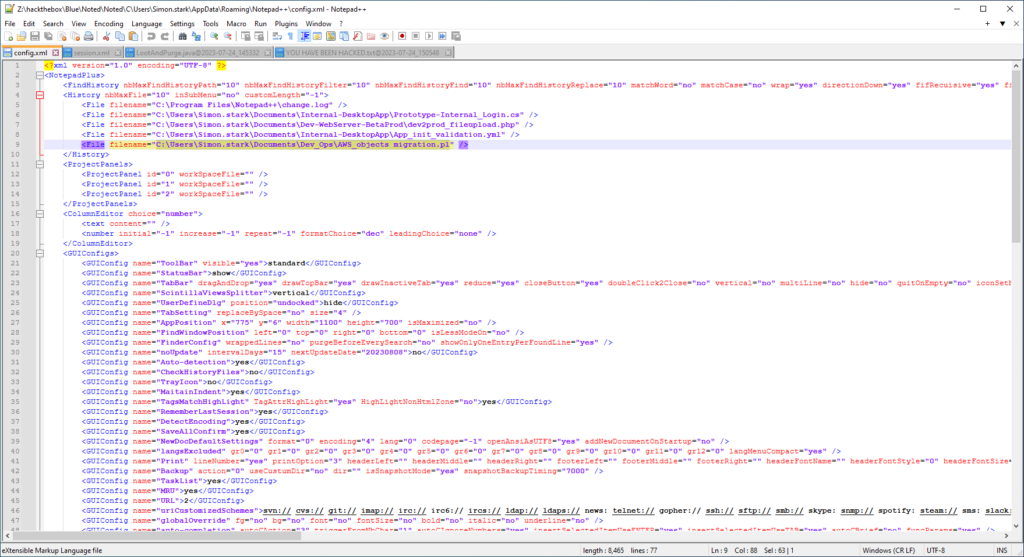
Answer: C:\Users\Simon.stark\Documents\Dev_Ops\AWS_objects migration.pl
Task 2 – … What is the full path of the program’s source file?
Going into the session.xml file I found the directory of the original LootAndPurge.java.
Answer: C:\Users\simon.stark\Desktop\LootAndPurge.java
Task 3 – What’s the name of the final archive file containing all the data to be exfiltrated?
Switching to LootAndPurge.java@2023-07-24_145332, I was able to find the line of code that defined the directory the archive would be saved in and the name of the file.
Answer: Forela-Dev-Data.zip
Task 4 – What’s the timestamp in UTC when attacker last modified the program source file?
This one was a little trickier and requires a little bit more than just finding the answer and pasting it. First, within session.xml I found originalFileLastModifTimestamp=”-1354503710″ and originalFileLastModifTimestampHigh=”31047188″. Each of these represent 32bits of the 64bit number that makes up the timestamp. So we need to combine the two numbers to get the full timestamp and then put the large number through a datetime function to get it into the format required for the question. I did this using the Python code below.
import datetime
timestamp_low = -1354503710
timestamp_high = 31047188
full_timestamp = (timestamp_high << 32) | (timestamp_low & 0xFFFFFFFF)
timestamp_seconds = full_timestamp / 10**7
timestamp = datetime.datetime(1601, 1, 1) + datetime.timedelta(seconds=timestamp_seconds)
print(timestamp)Answer: 2023-07-24 09:53:23
Task 5 – The attacker wrote a data extortion note after exfiltrating data. What is the crypto wallet address to which attackers demanded payment?
The next two questions require us to gain access to the password-protected pastbin(s) within YOU HAVE BEEN HACKED.txt@2023-07-24_150548. I found the line “String password = “sdklY57BLghvyh5FJ#fion_7″;” within LootAndPurge.java@2023-07-24_145332, my initial thought was that it was the password for the archive which that script was creating, however, after scrubbing through all of the other files I couldn’t find any other password so I just gave it a shot and it worked! After gaining access to the pastebin both answers for this question and the next one are just staring right at you.
Answer: 0xca8fa8f0b631ecdb18cda619c4fc9d197c8affca
Task 6 -What’s the email address of the person to contact for support?
As mentioned above the answer for this question is found in the same place as the last.
Answer: CyberJunkie@mail2torjgmxgexntbrmhvgluavhj7ouul5yar6ylbvjkxwqf6ixkwyd.onion
